How many times have you heard the your IT person or the media talk about server attacks or “DDoS” attacks? Perhaps you heard about websites operated by NATO getting hit with DDoS attacks in March of 2014. Or the attacks that hit Wells Fargo, PNC Bank and U.S. Bankcorp in September of 2012.
I’ve had a few clients ask me what these mysterious DDoS attacks are and if they are vulnerable, prompting me to do a write up on it…hopefully in layman’s terms.
Cyberterrorism and cybersecurity, which one could clarify this as, are big business these days, but we’ll get to that in a moment.
Let’s define what DDoS is first. To start, DDoS has nothing to do with the old Microsoft DOS operating system. DDoS stands for Distributed Denial of Service. It is a method of attacking a computer system by flooding it with so many messages it is obliged to shutdown, according to dictionary.com. Huh? Let’s break it down.
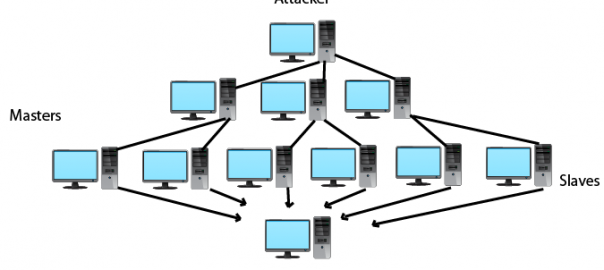
There are many ways a DDoS attack can occur. One way is for computers to be infected with a trojan virus. The virus is a small application that allows remote command-and-control capabilities of the computer without the user’s knowledge. The malicious hacker performs a DDoS attack by hijacking a fleet of remotely-controlled computers to send a flood of network traffic to a target server, known as server requests. The server becomes so bogged down by these server requests, it doesn’t have time to respond to legitimate users’ requests. That can cause the server to completely stop responding, resulting in your site and system going down.
Another DDoS tactic is utilizing websites, usually on open-source content management system (CMS) platforms such as WordPress and Joomla, to overload another server with bogus requests and information.
So why is it big business? Well to start, it’s no secret that hackers are often hired for corporate sabotage. They are paid (very well) to take down competitor websites and servers. So what do companies have to do? Hire security experts (who are also hackers…but the “good guys”) to combat the hired attackers. This stuff doesn’t come cheap.
It has also become a very real part of warfare, cyber warfare. DDoSing has been used by many governments to take down other systems. Remember the DDoS attacks in late 2012, early 2013 that took down more banks? The U.S. Government pointed the finger at Iran, “most likely in retaliation for economic sanctions and online attacks by the United States” according to this New York Times article.
So, now you’re probably wondering how you may be a part of the problem.
To start, do you have up-to-date anti-virus software on your computer? You may want to look into that and run a few scans.
Is your website built on an open-source CMS platform? If yes, your site may be used in a DDoS conspiracy. For example, any WordPress site with Pingback enabled, which is on by default, can be used in DDOS attacks against other sites.
How can you combat this? There are several steps you can take.
- When you write a new post, like we’re doing here, scroll down and look at your metaboxes. Do you see one that says “discussion?” If you don’t see it, click on screen options at the top right of your screen and enable the discussion tab. Now, take a look in the discussion metabox. You should see “Allow comments” and “Allow trackbacks and ping backs on this page.” Disable the trackbacks and ping backs. You should do this for old posts as well.
- Under the settings menu item, click on discussions. Unchecking “Allow link notifications from other blogs” will certainly turn off pingbacks for future posts, though you would still need to go in and edit existing posts to disable it for those.
- Create a plugin with the following filter:
add_filter( ‘xmlrpc_methods’, function( $methods ) {
unset( $methods[‘pingback.ping’] );
return $methods;
} );
If you don’t know how to create a plugin, we did it for you. Download the .zip file, unzip it and upload it to your plugins folder. Make sure to activate it as well. The code was taken from an article written by Sucuri, an internet security company.
If you’re using a different system, such as Joomla, there are other resources out there that will help you combat the use of your site in DDoS attacks.
So to sum it up, cyberattacks and cyberterrorism are real problems (or if being used to fight terrorism, maybe a good thing?). It is not only your server host’s problem, but yours too. While they are doing everything they can to protect your site and server, you need to help them by closing security holes that may exist in your website or on your computer.
It’s a team effort.